Authenticating a Google Cloud service
In order to run queries on your Google Cloud databases, such as Cloud Firestore and Realtime Database, Ezfire requires a service account credential with the appropriate permissions to access that database. There are two methods of providing the appropriate permissions to Ezfire, a delegate service account in our project or a service account key from your project. To learn more about how service accounts work on Google Cloud, check out this article.
Using the Delegate Service Account
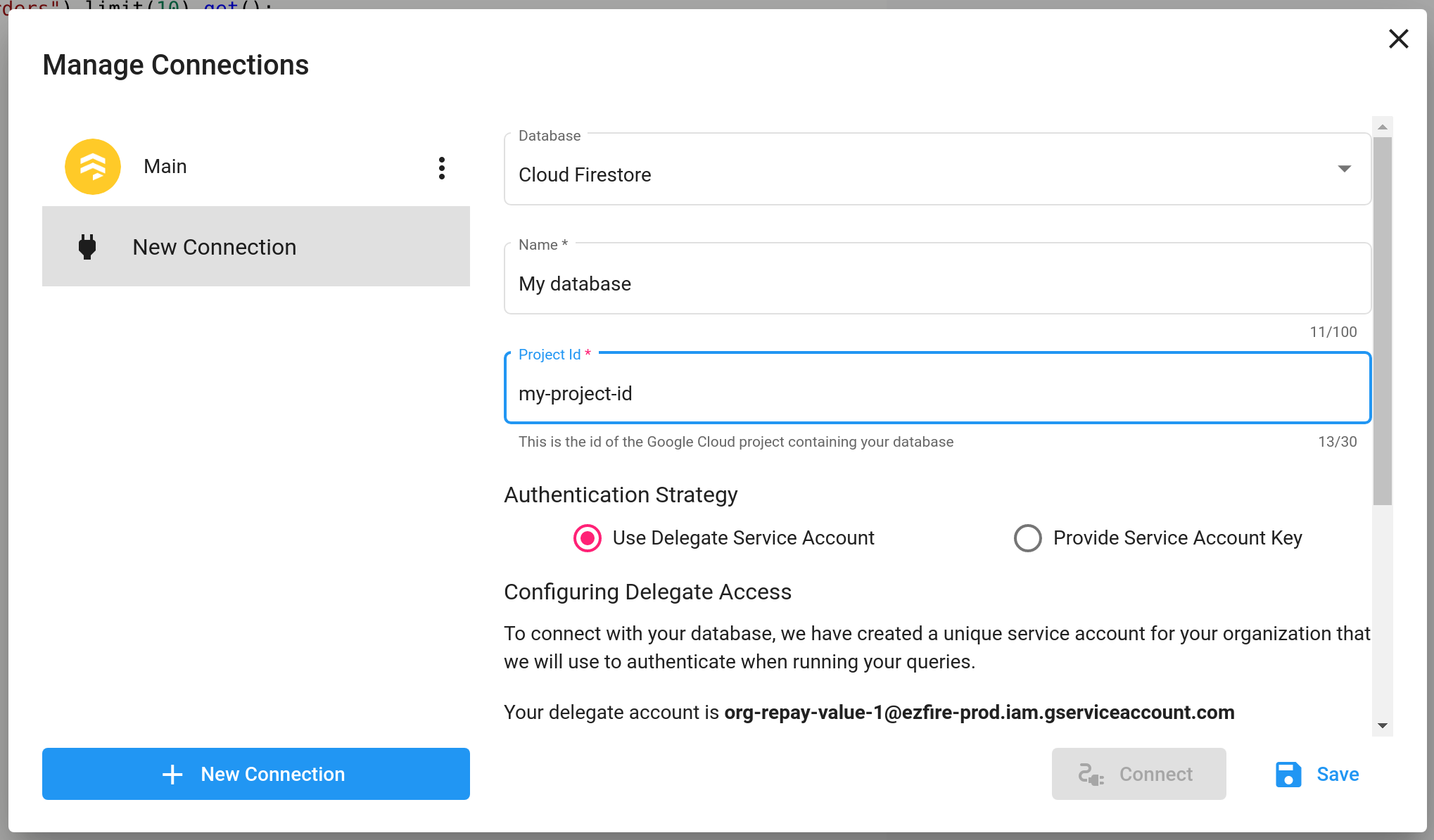
When using this strategy, we associate with your organization a unique service account in our project. You can add this service account as an IAM member to your project with the required permissions. When a connection is created with this strategy, we will use the delegate service account to access your database and execute your query. This is the recommended way of connecting with Ezfire, as it does not require you to expose any sensitive credentials.
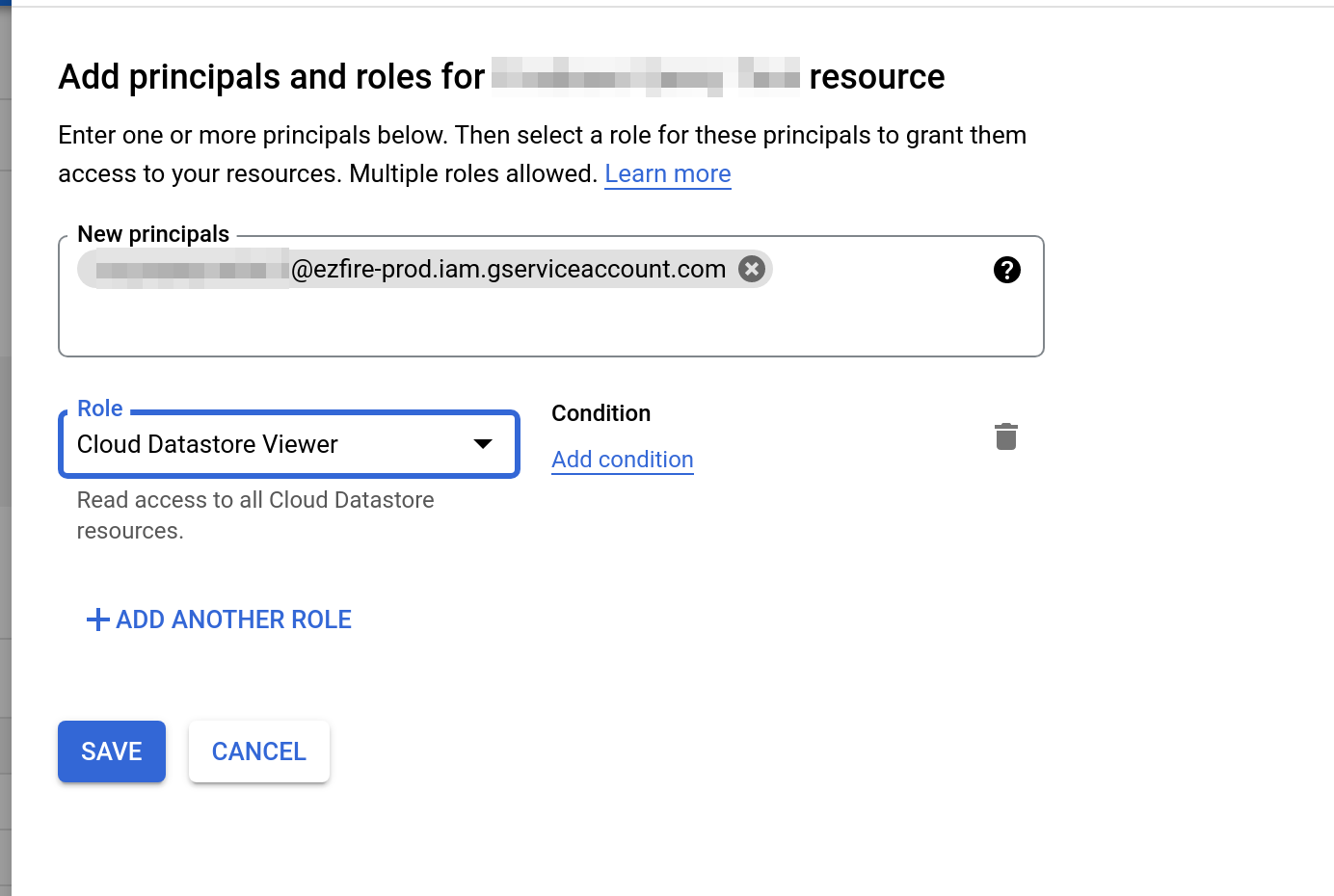
It is recommended that you give the delegate service account only the minimum amount of permissions required to run your queries. For example, if you only want a read-only connection to Cloud Firestore, the minimum required role is roles/datastore.viewer. For a read/write connection, the minimum required role is roles/datastore.user.
Provide a Service Account Key
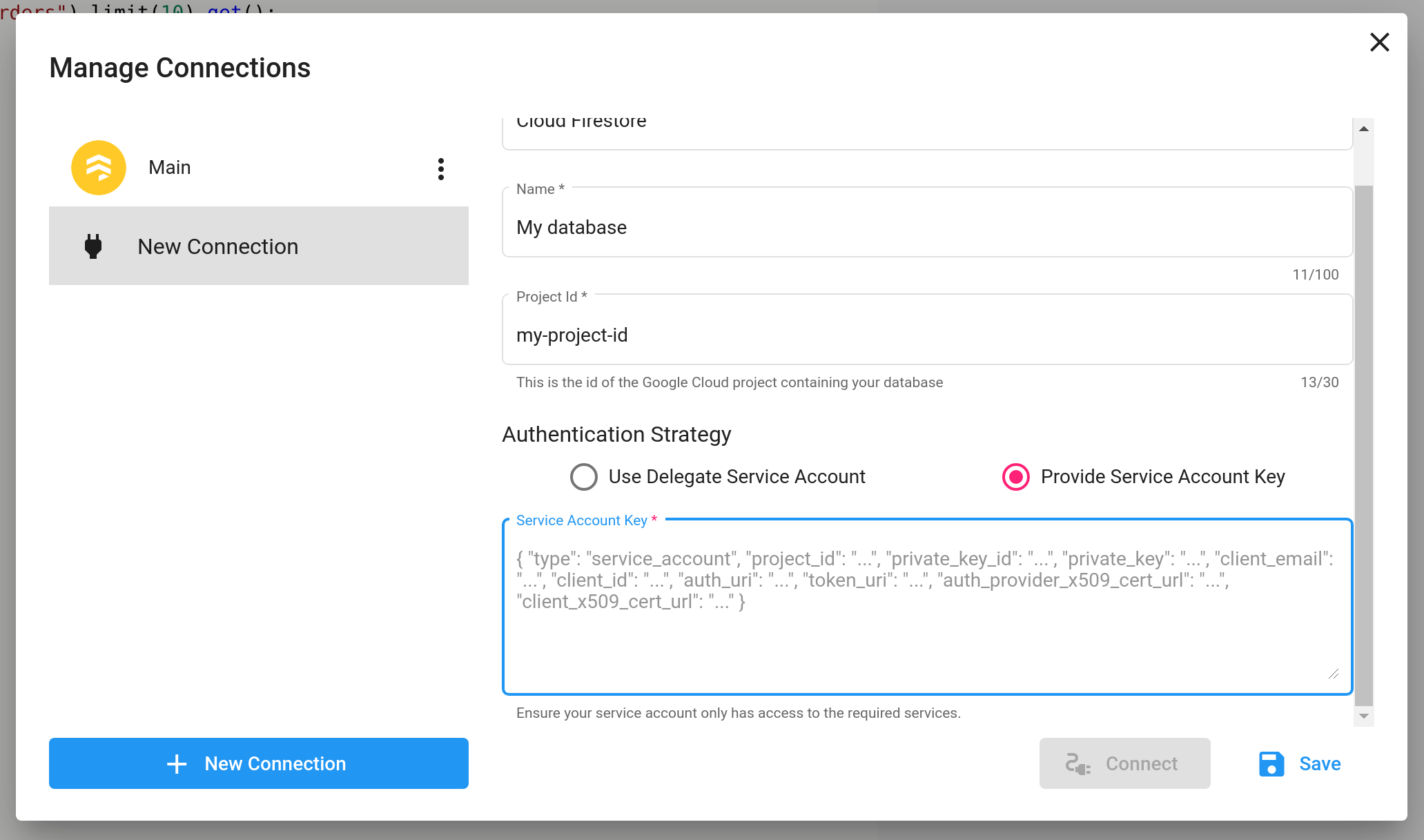
Alternatively, instead adding our service account as an IAM member to your project, you can create your a service account in your own project and provide us with a JSON service account key to use when running queries. It is not recommended to use this strategy unless you cannot use the delegate service account.
As with the delegate service account, it is recommended to only give the provided service account the minimum required permissions.